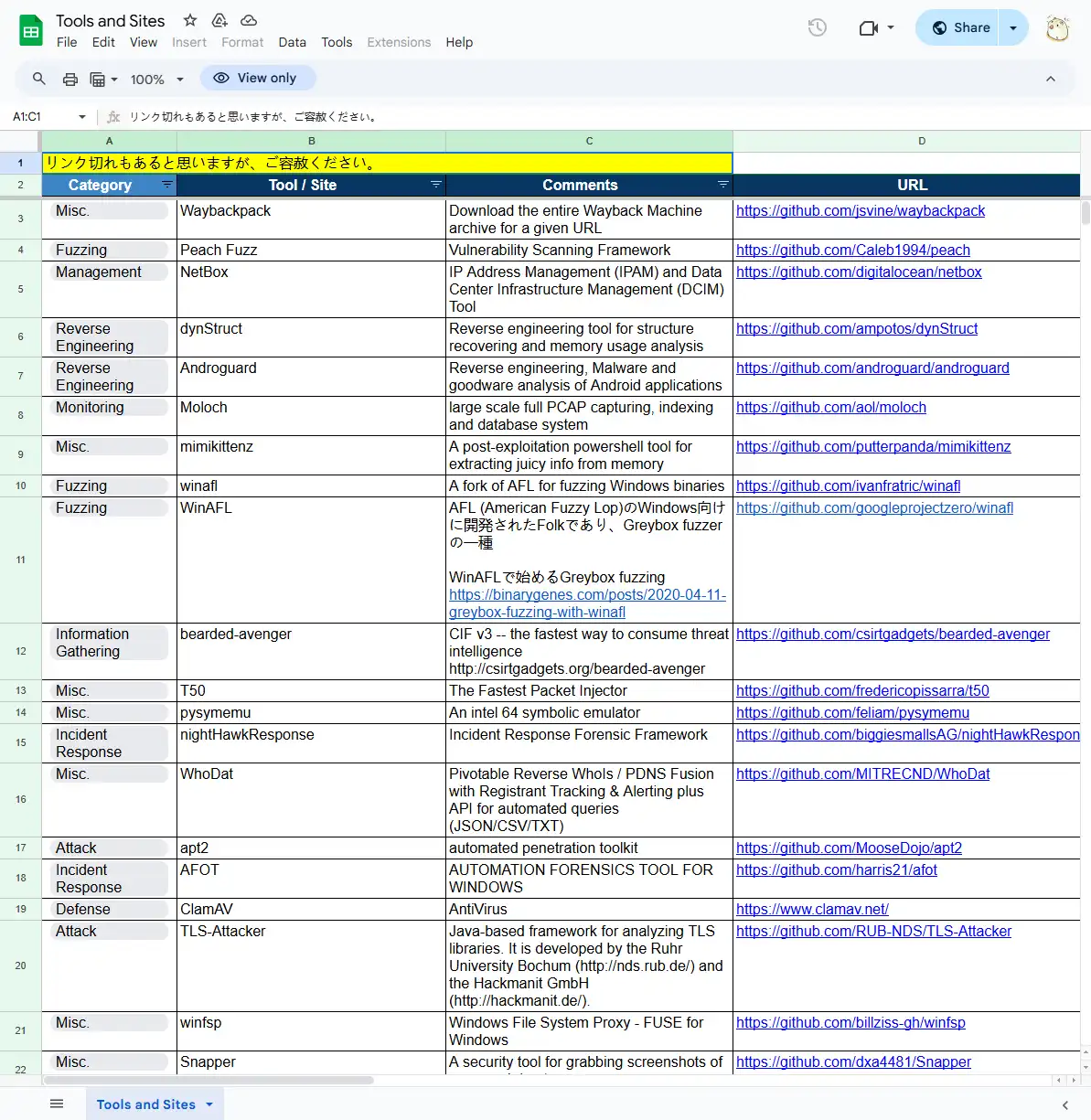
The document titled “Tools and Sites” is a Google Spreadsheet that compiles a comprehensive list of tools and resources across various categories, primarily focusing on cybersecurity and IT management.
Document Overview:
This spreadsheet categorizes tools into several main categories, including:
- Fuzzing: Tools like Peach Fuzz and WinAFL, which are used for vulnerability scanning and fuzz testing of Windows binaries.
- Management: Resources such as NetBox, an IP Address Management (IPAM) and Data Center Infrastructure Management (DCIM) tool.
- Reverse Engineering: Tools like dynStruct and Androguard, designed for structure recovery, memory usage analysis, and Android application analysis.
- Monitoring: Applications like Moloch, a large-scale full packet capture, indexing, and database system.
- Incident Response: Frameworks such as nightHawkResponse and AFOT, which assist in forensic analysis and incident response.
Each entry includes the tool’s name, a brief description, and a URL linking to the tool’s official page or repository.
Intended Audience:
This document is intended for cybersecurity professionals, IT managers, and researchers seeking a curated list of tools to support various aspects of cybersecurity, including vulnerability assessment, incident response, and system monitoring.
Use Cases:
- Tool Discovery: Assists professionals in identifying tools relevant to specific cybersecurity tasks or challenges.
- Resource Compilation: Serves as a centralized directory of cybersecurity tools, facilitating easy access and comparison.
- Skill Development: Provides resources for professionals looking to expand their expertise by exploring and utilizing different tools.
Document Evaluation:
The spreadsheet is well-organized, offering a broad spectrum of tools across different cybersecurity domains. The inclusion of direct links to each tool enhances its utility, allowing users to quickly access and evaluate potential solutions. However, the document could benefit from additional details such as user reviews, feature comparisons, or integration capabilities to further assist in decision-making. Overall, it serves as a valuable resource for cybersecurity professionals exploring tool options to enhance their operations.
Document URL
https://docs.google.com/spreadsheets/d/1H1h2OJXk6e_hxB6oQXVFTux8my3Seb6-p73aB2FBpc8/edit?gid=0#gid=0
Copyright Notice:
This article is collected from internet information by Mika and manually written and organized. Unauthorized reproduction is prohibited.